How to Protect Your Identity From Job Scammers
Scammers clone recruiter profiles to run job frauds. Learn how to verify your identity, document scam operations, and build protection platforms won't provide.
You open LinkedIn Monday morning and there it is: “You tried to scam me.”
Your stomach drops. Three more messages appear. Then seven. All angry. All accusing you of running fake interviews, requesting bank details, asking for payment to access “job opportunities.” Screenshots of conversations you never had. A job posting with your face on it.
You didn’t send any of this. Someone stole your identity. Cloned your profile or made a convincing fake. They’re targeting desperate job seekers with your name, your photo, your company logo. And now the victims found the real you.
You frantically scroll through accusations. More keep coming. Your professional reputation, built over years, is being weaponized to hurt people. HR has no protocol for this. LinkedIn’s report button feels like screaming into a void.
Most people try the obvious fixes. They all fail in predictable ways. The platforms that profit from open networks won’t protect you. The victims who need help can’t tell real from fake. And the scammers just keep making new accounts.
This isn’t about being more careful or better at crisis management. This is about a system designed to look trustworthy without actually ensuring trust. Here’s what’s really happening and what actually works when your professional identity becomes a weapon.
The Standard Playbook
Your first instinct is to report the fake profile and wait for the platform to handle it. This seems obvious. LinkedIn has a report button. They have policies against impersonation. Surely they’ll act quickly.
They won’t.
Your report disappears into an automated queue. Days pass. Maybe weeks. You get a generic response: “We’re reviewing this.” Meanwhile, the scammer is still active. Still using your face. Still contacting victims. The angry messages don’t stop.
When LinkedIn finally removes the profile, if they do, the scammer creates another one. Different email address, same stolen photo. They’re back in business by Tuesday. You’re playing whack-a-mole with no hammer and an endless supply of moles.
So you try transparency. You post a public warning on your real profile: “I’m being impersonated! I will never ask for money or bank details!” Surely this prevents confusion.
It doesn’t. The wrong people see it.
Worse, the scammer might copy your warning and add their own twist: “Unlike that fake profile claiming to be me...” Now there are two profiles, both claiming the other is fake. Victims have no idea who to trust. Your public warning just made you look less credible.
You can also contact every victim individually. They’re hurting and angry. They deserve a personal response. If you explain what happened, show empathy, surely they’ll understand you’re a victim too.
Some do. Many don’t.
Each conversation requires you to relive the violation, defend yourself, provide “proof” you’re real. A few people get angrier because “that’s exactly what a scammer would say.” You’re spending hours every day on this instead of doing your actual job.
And new victims keep appearing because the scammer is still out there. You burn out trying to repair damage you didn’t cause while the real problem continues unchecked.
Trust Arbitrage Is the Business Model
The problem isn’t individual scammers. It’s the machine they’re exploiting.
LinkedIn, Indeed, and job boards make money by creating open networks where people connect easily. Low friction equals more users, more engagement, more ad revenue. Their entire business model depends on making it simple to create profiles, reach out to strangers, and claim professional credentials.
But they don’t always verify identity. Verification costs money and slows growth. So the platform’s incentive is to look trustworthy without actually ensuring trust.
This creates an arbitrage opportunity. Scammers exploit the appearance of legitimacy without any actual verification barrier.
When something goes wrong, the platform has structured plausible deniability. Their terms of service say “report violations,” but there’s no service level agreement, no accountability, no dedicated response for identity theft. The burden falls entirely on you to prove the negative, that you’re NOT a scammer, which is nearly impossible.
Meanwhile, the victims have no recourse either. They can’t sue the platform. They can’t easily identify the real criminal behind anonymous emails and burner phones. So they attack the only visible target: the person whose identity was stolen.
The deeper structural reality makes it worse.
The job market manufactures desperation at scale. When you’ve been unemployed for months, when savings are running out, when you have a family depending on you, your judgment changes. You want to believe the opportunity is real. You ignore red flags.
Scammers don’t create this desperation. Endless applications into voids create it. Automated rejections create it. Algorithms that filter you out before a human ever sees your resume create it. Legitimate companies that ghost candidates after five interview rounds create it.
This environment trains job seekers to be grateful for any response, any human contact, any chance. It erodes their ability to distinguish real from fake because the real system already feels fake and dehumanizing.
The scam works because the legitimate hiring process has already broken people’s calibration. When normal recruitment feels like a scam, actual scams slip through.
New Newsletter
I wanted to let you know about something new! This newsletter will continue doing what it does best: helping you navigate the world of recruitment.
But I’ve also launched a second newsletter where I can dive into broader ideas and topics I’m passionate about. Would love to have you join me there too!
Where Most Job Scammers Actually Operate From
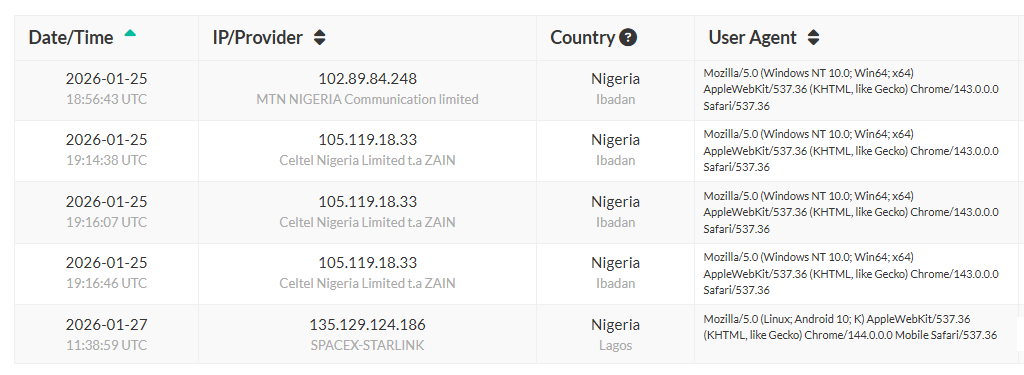
Over the last few years, I’ve done something most recruiters don’t. I replied to scam emails I found online in LinkedIn comments. And I engaged with people pretending to be me. Not to argue, but to find out where they operate.
Nine out of ten scammers I interacted with were in the same country. Different cities, but the same country every time.
Nigeria. Specifically Lagos and Ibadan.
This isn’t speculation. This is pattern recognition from years of tracking fake profiles, responding to fraudulent messages, and documenting where the conversations lead. The concentration is undeniable.
Note: The vast majority of people in Lagos and Ibadan are not scammers. They live normal lives. They work in business, tech, education, trade. They’re trying to build careers in cities where the global reputation makes that harder.
Why These Cities Became Fraud Hubs
Nigeria has been associated with advance-fee fraud since the “419 scams” of the 1990s. The country carries a global reputation as a scam capital, deserved or not.
Lagos is Nigeria’s commercial hub and largest city. It’s also home to organized cyber-fraud rings and “training schools” where so-called “Yahoo boys” learn to run online scams. These aren’t lone operators working from home. These are syndicates operating from rented offices and internet cafés, working across time zones, using forged documents and fake business proposals.
Law enforcement reports consistently list Lagos among the top cities for internet fraud arrests. Ibadan follows close behind.
The economic conditions make it easier. High youth unemployment. Limited legitimate opportunities. Weak regulatory enforcement. Fraud rings recruit young people who see scamming as their only path to income. The infrastructure exists. The knowledge gets passed down. The operations scale.
These cities didn’t become fraud centers by accident. They became fraud centers because the conditions allowed it, and the economics rewarded it.
The Reality Most People Miss
The concentration of fraud operations is real. And if your identity gets stolen by a job scammer, there’s a very high probability the person using your face is operating from one of these two cities.
This matters because it changes how you respond. You’re not dealing with a random individual. You’re dealing with organized operations that have infrastructure, training, and volume. They’ll recreate profiles faster than platforms can take them down. They’ll adapt their scripts when one approach stops working. They have backup accounts ready.
Understanding where the problem concentrates doesn’t solve it. But it stops you from treating this like a one-off incident you can report and forget.
Scammers Now Copy Your Writing Style and Email Signatures
Over the last few years, scammers have evolved their operations. I won’t share every detail because some of them read these newsletters and I’m not giving them a playbook. But one tactic deserves attention because it’s working.
They’re using content from your newsletters, email signatures, and public writing to make their fake emails more convincing. They study how you communicate. They lift phrases you use. They mimic your tone and formatting.
Scammers can steal email signatures from real people (like Katrina) by copying them and then modifying them to include fake information, such as a fraudulent email address. This tactic is often used to make phishing emails appear more legitimate and trick recipients into trusting the sender.
If you offer resume reviews, work as a recruiter, or coach job seekers, and you still do not use a domain name, it is the right time to get one. Ditch Gmail. Ditch Outlook.
Gmail is one of the most common email addresses used in these scams. When your communications come from a free email service, you make the scammer’s job easier. There’s no verification barrier. Anyone can create a fake email address and sound just like you.
A domain you own, yourname.com or yourcompany.com, creates a verification checkpoint scammers can’t easily fake. It signals legitimacy in a way free email never will.
Keep Your Channels Open for Reports
The best defense isn’t locking down all contact methods. It’s staying accessible so people can reach you when something’s wrong.
Keep your website contact form active. Keep LinkedIn messages open. Keep your social accounts reachable. When someone contacts you saying they think they’ve been scammed by “you,” that’s valuable intelligence.
Ask them for screenshots. Ask for the exact email address being used. Ask for email headers, which show the IP address and routing information behind the message. This data tells you what infrastructure the scammer is using.
Once you have it, you can take action. If they’re using a domain name hosted on a web hosting service, report both the domain and the hosting company. These companies respond quickly because they don’t want to harbor fraud operations.
If they’re using Gmail, the reporting process exists but moves slower. Still worth doing.
The pattern is simple: stay reachable, collect evidence, report systematically. Each report makes it slightly harder for that specific operation to continue. It won’t stop all scammers, but it stops that one.
How To Report Scams To Google
If you report the scam to Google, you will receive a response with detailed instructions on how to proceed.
Google Instructions:
We understand your concern that someone is scamming job seekers via email they created with your name. We are more than willing to assist you. Let’s work on this together.
Having your name attached to a job scam not only risks the safety of others but also feels like a personal violation of your reputation.
Since the scammer is using a Gmail address specifically, you have a direct line to report them to Google, as well as several law enforcement channels. Here is how to take action:
Report the Email Address to Google
Google has a specific reporting flow for users who are impersonating others or conducting scams.
Use the Gmail Abuse Form: Go to the Report abuse from a Gmail account.
Select “Impersonation”: Choose the option that indicates someone is pretending to be you or using your identity for fraudulent purposes.
Provide Headers: If you can get a copy of one of the scam emails (perhaps from a victim who reached out to you), include the “Email Headers.” This contains the technical data Google needs to trace the account’s origin.
Protect Your Reputation
To prevent people from falling for this in the future, you should create a “paper trail” online:
Update LinkedIn/Social Media: Post a brief notice: “Scam Alert: Someone is using the email jantegzehiringmanager@ to pose as me. Please note I only communicate via [Your Official Domain] and never ask for payment or sensitive info during interviews.”
Search Engine “Dead Ends”: If you have a personal website or portfolio, add a small disclaimer in the footer. If victims Google your name + “hiring manager,” they may find your warning first.
Alert Targeted Platforms
Scammers usually find victims on job boards. If you know which sites they are using (LinkedIn, Indeed, Monster), contact those platforms’ support teams to let them know a fraudulent “Hiring Manager” is using your name to lure candidates.
We appreciate your patience and understanding in this matter. Please don’t hesitate to reply to this email if the issue isn’t resolved or if you have more questions and we’ll be happy to help. We are also happy to direct you to our comprehensive support page, which may be able to answer your questions immediately: Google Help Center.
Google makes it a top priority to provide accurate and correct information to our customers, and we are always looking for ways to improve your satisfaction.
Within 48 hours of our last interaction, you’ll receive a short survey via email. We would love to hear your feedback about our interaction today and your overall experience with Google Support.
What You Can Do
These scams are only going to get more common, especially with AI in the mix. The best move you can make right now is to verify your LinkedIn profile and set up a domain name with a contact form so people can reach you directly. Honestly, just expect this to happen eventually, especially as you get more active and visible on social media.
When you discover a fake profile, don’t just report it. Document everything. Screenshots with timestamps. Archived versions of the fake profile. Examples of the scam messages. Victim testimonials if they’re willing to share.
You can also create a simple one-page document titled “Current Impersonation Alert” with all this evidence. Share the link publicly. This serves three purposes: victims who search your name find it immediately, it demonstrates you’re proactive rather than defensive, and law enforcement or platform investigators have everything in one place.
The Platforms Could Stop This Tomorrow
LinkedIn, Indeed, ZipRecruiter have the data. They can see when a profile is created with a stolen photo. They can detect when someone messages 50 job seekers in an hour asking for bank details. They can identify patterns that scream “scammer” with 99% accuracy: new account, no connections, mass messaging, requests for money or using the same message as previously reported accounts.
The technology exists. They use similar detection for spam and bot accounts. They could stop this way more effectively.
When your identity gets stolen, the platform’s response is designed to minimize liability, not solve the problem. “We take this seriously” means “we’ve done the legal minimum to avoid being sued.” The report button exists so they can say they have a process. The process exists to protect the company, not you.
The uncomfortable truth is that you’re on your own. The platform won’t save you. The victims can’t help you. The scammers won’t stop. Your only option is to build your own infrastructure for trust outside the system that failed you.
It shouldn’t be this way. But it is.
Bonus: How I Actually Track These Scammers
Most people report and hope. I hunt.
Here is how you can do it.